

For IT leaders and contact center directors in banking, understanding the difference between SOC and PCI security determines vendor risk exposure. This article examines both frameworks, explains when each applies, and shows why PCI DSS Level 1 certification matters for customer interaction platforms.
SOC and PCI Are Often Confused: Here’s Why
Security certifications blend together in vendor presentations. Both SOC 2 and PCI DSS involve audits. Both produce official reports. Both appear in vendor security documentation.
Many technology providers present their SOC 2 Type II report as equivalent to PCI DSS Level 1 certification. But there’s just one problem: They’re not equivalent.
One big difference? Ongoing due diligence. SOC 2 verifies a vendor follows their stated security practices. PCI DSS Level 1 enforces specific controls with continuous testing.
Financial institutions discover this gap after integrating vendors who can't meet compliance requirements. Contact center platforms handling member authentication or payment confirmations need proper certification. The difference between SOC vs PCI determines your regulatory exposure.
Put simply, SOC leaves you far more exposed—while PCI ensures you are far more secure.
What Does SOC 2 Cover?
SOC 2 evaluates controls around five trust service criteria, developed by the American Institute of CPAs:
- Security
- Availability
- Processing integrity
- Confidentiality
- Privacy
Type I reports capture controls at a single point in time. Type II extends coverage to six or twelve months. Auditors review policies, interview staff, and test sample transactions.
SOC 2 Flexibility Creates Gaps
The framework allows companies to define their own controls. Two vendors could achieve SOC 2 with vastly different architectures. One uses basic firewalls while another implements zero-trust networking— both pass if controls match their policies.
SOC 2 doesn't mandate:
- Network segmentation standards
- Specific encryption requirements
- Vulnerability scanning frequency
- Penetration testing methodology
- Incident response timelines
For platforms handling financial data, these gaps create risk. IT leaders evaluating the difference between SOC and PCI security should consider whether flexible controls meet their needs.
What Does PCI DSS Level 1 Require?
PCI DSS Level 1 mandates prescriptive technical requirements with continuous validation. The Payment Card Industry Security Standards Council developed these standards for organizations handling cardholder data.
Level 1 applies to:
- Organizations processing over six million transactions annually
- Service providers storing, processing, or transmitting cardholder data
- Platforms touching authentication workflows or payment confirmations
Technical requirements
Network segmentation Cardholder data environments must remain isolated. Quarterly tests verify segmentation effectiveness.
Vulnerability management
- Quarterly external scans by Approved Scanning Vendors
- Monthly internal vulnerability assessments
- Annual penetration testing of network and applications
- Critical patches deployed within 30 days
Access controls
- Multi-factor authentication for administrative access
- Least-privilege permissions with documented justification
- Split knowledge and dual control for encryption keys in cardholder environments
- Comprehensive logging of all access attempts
Encryption standards
- Strong cryptography for data at rest (AES-256 or equivalent)
- TLS 1.2 minimum for transmission (TLS 1.3 encouraged in PCI DSS 4.0)
- Hardware security modules for key management
- Documented key rotation schedules
Compliance requires daily attention. Quarterly scans, monthly reviews, and continuous monitoring create an operational rhythm.
Miss a scan or let a certificate expire? You're out of compliance—and into trouble.
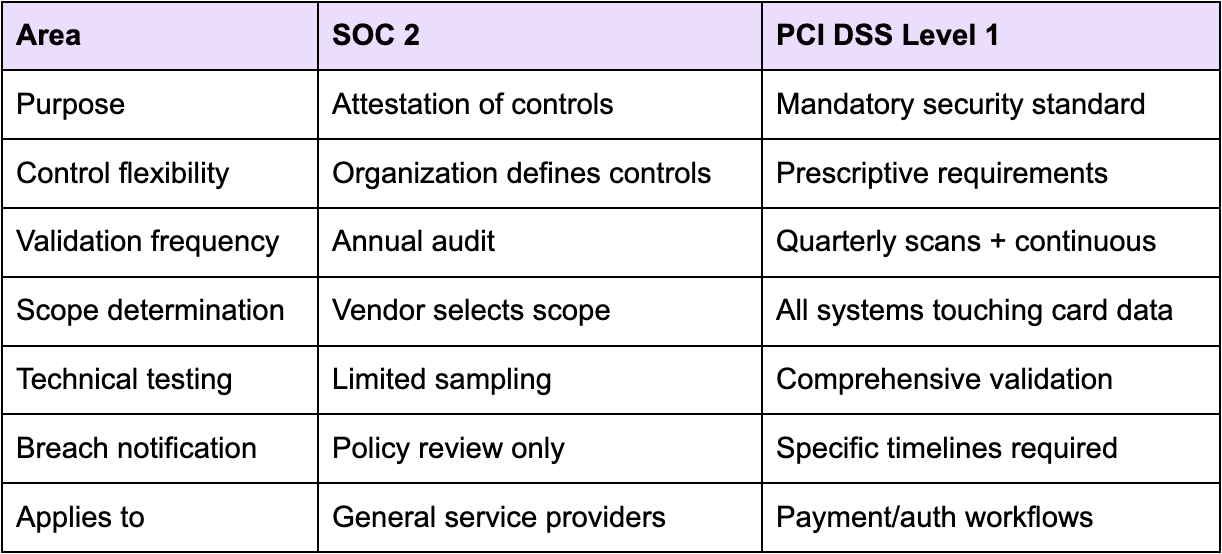
SOC vs PCI: Key Differences for Financial Institutions
Understanding SOC vs PCI helps evaluate vendor risk. Here's what matters for banks and credit unions:
Comparison table
Practical Implications
Audit requirements differ significantly
SOC 2 produces narrative reports. PCI generates technical findings with pass/fail determinations.
Risk exposure varies
SOC 2-only vendors might handle authentication with basic controls. When examiners review vendor management, they expect equivalent standards to internal requirements.
Integration complexity changes
PCI-compliant vendors already implement required segmentation and encryption. SOC 2 vendors may need compensating controls.
When Do Vendors Need PCI DSS?
Payment processing triggers obvious PCI requirements. Digital engagement platforms present complex scenarios where requirements aren't immediately clear.
CoBrowsing Scenarios
Agents guide customers through online banking. The platform might mask payment fields but operates in the same browser context. Without proper controls, the system could access card data.
PCI DSS Level 1 ensures technical prevention. SOC 2 only confirms policy against accessing data.
Voice Interactions
Contact center platforms processing phone keypad entries handle DTMF tones containing card numbers. Even without storage, real-time processing requires PCI controls.
Authentication Workflows
Identity verification gates payment access. Knowledge-based authentication, one-time passwords, and biometric confirmation all control payment functionality. Security failures enable unauthorized payment access.
Screen Sharing Risks
Remote assistance lets agents see customer screens. Every support session creates potential data exposure. PCI requires technology preventing capture, mandating encryption, and maintaining audit trails.
The determining factor: Could the vendor potentially access payment data? Regulators don't distinguish between intended and possible access.
How Glia Maintains PCI DSS Level 1
Achieving PCI DSS Level 1 requires fundamental security architecture commitments.
Network Architecture
Cardholder data environments remain completely segmented. Firewall rules restrict traffic to essential communications only. Penetration tests validate isolation quarterly.
Data Protection
All data receives appropriate encryption:
- AES-256 or equivalent for data at rest
- TLS 1.2+ for transmission (supporting TLS 1.3)
- Hardware security modules managing keys
- Certificate pinning preventing interception
Access Management
Zero-trust principles govern all access:
- Hardware tokens for production changes
- Time-boxed maintenance windows
- Role-based permissions tied to job functions
- Complete audit trails for every attempt
Continuous Validation
Security posture undergoes constant verification:
- Approved Scanning Vendors perform quarterly external scans
- Internal teams conduct monthly assessments
- Critical systems receive weekly reviews
- Penetration testing occurs annually minimum
Change Control
Every production modification requires:
- Formal approval documentation
- Testing in isolated environments
- Validated rollback procedures
- Configuration standard compliance
Physical security extends beyond data centers to development environments and corporate facilities. Badge access, surveillance, and environmental monitoring create defense layers.
SOC 2 vs. PCI for IT leaders
Vendor certifications directly impact your risk profile and operational flexibility.
Regulatory Implications
Vendor findings consistently rank among top examination issues. Different security standards for sensitive data systems raise examiner questions. PCI-certified vendors demonstrate equivalent controls to internal requirements.
Integration Considerations
PCI-compliant vendors reduce implementation complexity. Their existing controls align with your requirements. SOC 2 vendors might need additional security layers or restricted functionality.
Operational Burden
PCI vendors maintain quarterly validation. External assessors regularly confirm their compliance. SOC 2's annual cycle leaves gaps requiring intensive monitoring.
Risk Calculations
Cyber insurance providers factor vendor standards into coverage decisions. PCI-certified ecosystems demonstrate mature risk management. Mixed certification levels create concentration points limiting coverage.
Total Cost Analysis
SOC 2 vendors offer attractive rates initially. But hidden costs emerge through:
- Additional security tooling
- Expanded audit scope
- Specialized monitoring requirements
- Compensating control maintenance
Once you factor in potential breach costs, the economic argument becomes clear.
Future Flexibility
That innovative SOC 2 platform meets today's needs. What happens when adding payment processing? When regulators mandate stronger authentication? PCI foundations enable expansion without overhauls.
Vendor Evaluation Checklist
Ask these questions before selecting technology partners:
Certification Verification
- Request current Attestation of Compliance for PCI DSS Level 1
- Verify assessor credentials through official bodies
- Check certification dates for coverage gaps
- Confirm no limitations or qualifications
Scope Clarity
- Which systems fall under certification?
- Does your use case fit within certified scope?
- Request network diagrams showing segmentation
- Verify all intended features are covered
Technical Assessment
- How do they encrypt data in transit and rest?
- What key management procedures exist?
- Who performs vulnerability scanning and when?
- Can they provide sanitized penetration test results?
Incident Capabilities
- What are breach notification timelines?
- How do they classify security events?
- Who leads incident response?
- What's their incident history for 24 months?
Compliance Maintenance
- How do they maintain compliance between audits?
- What triggers re-assessment?
- Who monitors compliance drift?
- What self-assessment procedures exist?
Integration Requirements
- Which security controls must you implement?
- Are there network connectivity constraints?
- Will exceptions to your policies be needed?
- What compensating controls do they suggest?
Audit Support
- Will they provide evidence for your examinations?
- What SLAs exist for audit requests?
- Can they provide references from recent exams?
- How do they handle findings involving their platform?
SOC 2 and PCI DSS: The Final Verdict
Understanding the difference between SOC and PCI security protects your institution from vendor-related risk. For banks and credit unions enabling digital experiences, proper certification indicates whether partners share your security commitment.
Ready to explore how PCI DSS Level 1 security standards strengthen digital member engagement while simplifying compliance? Our security team can walk through Glia's comprehensive framework and demonstrate how proper certification eliminates vendor risk management complexity.
Frequently Asked Questions
What is the main difference between SOC 2 and PCI DSS?
The main difference between SOC 2 and PCI DSS lies in flexibility versus prescription. SOC 2 allows companies to define their security controls within broad categories. PCI DSS Level 1 mandates specific technical requirements with continuous validation through quarterly scanning and annual testing.
Do all financial services vendors need PCI compliance?
Financial services vendors need PCI compliance when they could potentially access, store, or transmit payment card data. This includes platforms handling digital engagement, authentication systems, or any workflows touching payment-related information.
Can SOC 2 replace PCI DSS requirements?
SOC 2 cannot replace PCI DSS requirements for systems handling payment data. While SOC 2 provides security attestation, it lacks the prescriptive controls and continuous validation PCI DSS requires for protecting cardholder information.
How often is PCI compliance validated?
PCI compliance validation happens continuously, not just annually. Level 1 requires quarterly external vulnerability scans, annual penetration testing, and monthly internal reviews. Significant changes trigger immediate revalidation.
What happens when vendors lose PCI certification?
When vendors lose PCI certification, financial institutions face immediate compliance gaps. Banks must implement compensating controls, restrict vendor access to sensitive data, or transition to compliant providers to maintain regulatory standing.
.avif)


.avif)





